WiMAX MAC Layer
The OSI model separates the functions of different protocols into a series of layers, each layer using only the functions of the layer below and exporting data to the layer above. For example, the IP (Internet Protocol) is in Layer 3, or the Routing Layer. Typically, only the lower layers are implemented in hardware while the higher layers are implemented in software.
The two lowest layers are then the Physical (PHY) Layer, or Layer 1, and the Data Link Layer, or Layer 2. IEEE 802 splits the OSI Data Link Layer into two sublayers named Logical Link Control (LLC) and Media Access Control (MAC). The PHY layer creates the physical connection between the two communicating entities (the peer entities), while the MAC layer is responsible for the establishment and maintenance of the connection (multiple access, scheduling, etc.).
The IEEE 802.16 standard specifies the air interface of a fixed BWA system supporting multimedia services. The Medium Access Control (MAC) Layer supports a primarily point-to-multipoint (PMP) architecture, with an optional mesh topology (see Section 3.7). The MAC Layer is structured to support many physical layers (PHY) specifi ed in the same standard. In fact, only two of them are used in WiMAX.
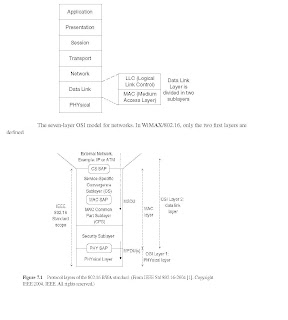
The protocol layers architecture defined in WiMAX/802.16 is shown in Figure 3.2. It can be seen that the 802.16 standard defines only the two lowest layers, the PHYsical Layer and the MAC Layer, which is the main part of the Data Link Layer, with the LLC layer very often applying the IEEE 802.2 standard. The MAC layer is itself made of three sub-layers, the CS (Convergence Sublayer), the CPS (Common Part Sublayer) and the Security Sublayer. The dialogue between corresponding protocol layers or entities is made as follows. A Layer X addresses an XPDU (Layer X Protocol Data Unit) to a corresponding Layer X (Layer X of the peer entity). This XPDU is received as an (X-1)SDU (Layer X-1 Service Data Unit) by Layer X-1 of the considered equipment. For example, when the MAC Layer of an equipment sends an MPDU (MAC PDU) to a corresponding equipment, this MPDU is received as a PSDU (PHYsical SDU) by the PHYsical Layer . Each of these layers or sublayers and many of their functions are described in the following sections.
The two lowest layers are then the Physical (PHY) Layer, or Layer 1, and the Data Link Layer, or Layer 2. IEEE 802 splits the OSI Data Link Layer into two sublayers named Logical Link Control (LLC) and Media Access Control (MAC). The PHY layer creates the physical connection between the two communicating entities (the peer entities), while the MAC layer is responsible for the establishment and maintenance of the connection (multiple access, scheduling, etc.).
The IEEE 802.16 standard specifies the air interface of a fixed BWA system supporting multimedia services. The Medium Access Control (MAC) Layer supports a primarily point-to-multipoint (PMP) architecture, with an optional mesh topology (see Section 3.7). The MAC Layer is structured to support many physical layers (PHY) specifi ed in the same standard. In fact, only two of them are used in WiMAX.
The protocol layers architecture defined in WiMAX/802.16 is shown in Figure 3.2. It can be seen that the 802.16 standard defines only the two lowest layers, the PHYsical Layer and the MAC Layer, which is the main part of the Data Link Layer, with the LLC layer very often applying the IEEE 802.2 standard. The MAC layer is itself made of three sub-layers, the CS (Convergence Sublayer), the CPS (Common Part Sublayer) and the Security Sublayer. The dialogue between corresponding protocol layers or entities is made as follows. A Layer X addresses an XPDU (Layer X Protocol Data Unit) to a corresponding Layer X (Layer X of the peer entity). This XPDU is received as an (X-1)SDU (Layer X-1 Service Data Unit) by Layer X-1 of the considered equipment. For example, when the MAC Layer of an equipment sends an MPDU (MAC PDU) to a corresponding equipment, this MPDU is received as a PSDU (PHYsical SDU) by the PHYsical Layer . Each of these layers or sublayers and many of their functions are described in the following sections.
Convergence Sublayer (CS)
The service-specific Convergence Sublayer (CS), often simply known as the CS, is just above the MAC CPS sublayer ( The CS uses the services provided by the MAC CPS, via the MAC Service Access Point (SAP). The CS performs the following functions:
The service-specific Convergence Sublayer (CS), often simply known as the CS, is just above the MAC CPS sublayer ( The CS uses the services provided by the MAC CPS, via the MAC Service Access Point (SAP). The CS performs the following functions:
Accepting higher-layer PDUs from the higher layers. In the present version of the standard [1], CS specifications for two types of higher layers are provided: the asynchronous transfer mode (ATM) CS and the packet CS. For the packet CS, the higher-layer protocols may be IP v4 (version 4) or v6 (version 6).
Classifying and mapping the MSDUs into appropriate CIDs (Connection IDentifier). This is a basic function of the Quality of Service (QoS) management mechanism of 802.16 BWA.
Processing (if required) the higher-layer PDUs based on the classifi cation.
An optional function of the CS is PHS (Payload Header Suppression), the process of suppressing repetitive parts of payload headers at the sender and restoring these headers at the receiver.
.
.
Delivering CS PDUs to the appropriate MAC SAP and receiving CS PDUs from the peer entity.
Medium Access Control Common Part Sublayer (MAC CPS)
The Common Part Sublayer (CPS) resides in the middle of the MAC layer. The CPS represents the core of the MAC protocol and is responsible for:
• bandwidth allocation;
• connection establishment;
• maintenance of the connection between the two sides.
The 802.16-2004 standard defines a set of management and transfer messages. The management messages are exchanged between the SS and the BS before and during the establishment of the connection. When the connection is realised, the transfer messages can be exchanged to allow the data transmission. The CPS receives data from the various CSs, through the MAC SAP, classified to particular MAC connections. The QoS is taken into account for the transmission and scheduling of data over the PHY Layer. The CPS includes many procedures of different types: frame construction, multiple access, bandwidth demands and allocation, scheduling, radio resource management, QoS management, etc
The Common Part Sublayer (CPS) resides in the middle of the MAC layer. The CPS represents the core of the MAC protocol and is responsible for:
• bandwidth allocation;
• connection establishment;
• maintenance of the connection between the two sides.
The 802.16-2004 standard defines a set of management and transfer messages. The management messages are exchanged between the SS and the BS before and during the establishment of the connection. When the connection is realised, the transfer messages can be exchanged to allow the data transmission. The CPS receives data from the various CSs, through the MAC SAP, classified to particular MAC connections. The QoS is taken into account for the transmission and scheduling of data over the PHY Layer. The CPS includes many procedures of different types: frame construction, multiple access, bandwidth demands and allocation, scheduling, radio resource management, QoS management, etc
Security Sublayer
The MAC Sublayer also contains a separate Security Sublayer providing authentication, secure key exchange, encryption and integrity control across the BWA system. The two main topics of a data network security are data encryption and authentication. Algorithms realising these objectives should prevent all known security attacks whose objectives may be denial of service, theft of service, etc.
In the 802.16 standard, encrypting connections between the SS and the BS is made with a data encryption protocol applied for both ways. This protocol defines a set of supported cryptographic suites, i.e. pairings of data encryption and authentication algorithms. An encapsulation protocol is used for encrypting data packets across the BWA. This protocol defi nes a set of supported cryptographic suites, i.e. pairings of data encryption and authentication algorithms. The rules for applying those algorithms to an MAC PDU payload are also given.
An authentication protocol, the Privacy Key Management (PKM) protocol is used to provide the secure distribution of keying data from the BS to the SS. Through this secure key exchange, due to the key management protocol the SS and the BS synchronize keying data. The basic privacy mechanisms are strengthened by adding digital-certifi cate-based SS authentication to the key management protocol. In addition, the BS uses the PKM protocol to guarantee conditional access to network services. The 802.16e amendment defi ned PKMv2 which has the same framework as PKM, re-entitled PKMv1, with some additions such as new encryption algorithms, mutual authentication between the SS and the BS, support for a handover and a new integrity control algorithm.
The MAC Sublayer also contains a separate Security Sublayer providing authentication, secure key exchange, encryption and integrity control across the BWA system. The two main topics of a data network security are data encryption and authentication. Algorithms realising these objectives should prevent all known security attacks whose objectives may be denial of service, theft of service, etc.
In the 802.16 standard, encrypting connections between the SS and the BS is made with a data encryption protocol applied for both ways. This protocol defines a set of supported cryptographic suites, i.e. pairings of data encryption and authentication algorithms. An encapsulation protocol is used for encrypting data packets across the BWA. This protocol defi nes a set of supported cryptographic suites, i.e. pairings of data encryption and authentication algorithms. The rules for applying those algorithms to an MAC PDU payload are also given.
An authentication protocol, the Privacy Key Management (PKM) protocol is used to provide the secure distribution of keying data from the BS to the SS. Through this secure key exchange, due to the key management protocol the SS and the BS synchronize keying data. The basic privacy mechanisms are strengthened by adding digital-certifi cate-based SS authentication to the key management protocol. In addition, the BS uses the PKM protocol to guarantee conditional access to network services. The 802.16e amendment defi ned PKMv2 which has the same framework as PKM, re-entitled PKMv1, with some additions such as new encryption algorithms, mutual authentication between the SS and the BS, support for a handover and a new integrity control algorithm.









[get this widget]